How to facilitate the use of Biometric identification in access control with STiD Readers ?
Using biometric credentials to enhance the security of your access control system requires a careful approach.
Any organization implementing such system must comply with data privacy regulations and should hence master every aspect of the data security management.
The transport, storage, protection, and anonymization of the biometric data is a most sensitive issue.

High Security
The Architect® RFID and NFC multi-technology readers are equipped with a biometrics module to read fingerprints and the highest standards to protect the data:
- The reader supports the latest contactless technologies with the newest data security devices:
–MIFARE® DESFire® EV2 & EV3 for the data encryption between the card and the reader - OSDP or SSCP protocol to secure the communication between the reader and the controller.
- Each Architect reader alsointegrates an EAL5+ certified crypto-processorto enhance protection levels and security key management.
Easy fingerprint management
Different possibilities of fingerprint management depending on your security needs:
-
Fingerprint templates directly stored in the RFID card:
–this is the easiest way to secure your biometric data, as the fingerprints are encrypted and stored directly in the access card. Such approach is compliant with the French CNIL & GDPR European legislation.
– The biometric reader will read fingerprint templates encrypted in the RFID card for a 1:1 verification. You may save and verify one or up to five fingers per user depending on your security needs.
– No private data is sent to any system or stored on a server or device.. Montage Bio Elogo

- Smartphone with biometric unlocking or Smartphone only with derogation:
– Virtual cards stored in a secured application can be used instead of the standard plastic card for the same level of security and without the need of a biometric unit at the reader.
–The reader can force the user to unlock the application on the smartphone also with his fingerprint. -
multi-factor identification of users::
– CWhen equipped with a backlit keypad, the reader allows multi-factor identification of users by combining the reading of an RFID or virtual card with the input of a personal keypad code.
– Thanks to its different operating modes, the keypad can be used for identification or to activate additional functions (alarm…)..

Advanced anti-fraud functions
The Architect® Blue biometric reader is designed to resist fraud attempts: False finger detection: the reader detects a wide range of counterfeit fingerprints made of latex, Kapton, transparent film, rubber, graphite, etc. Detection of live fingers Duress finger: the admin can assign a finger number dedicated to authentication when the user is threatened.

Ultimate self-protection
The patented motion sensor pull detection system protects sensitive data by allowing authentication keys to be erased. Unlike existing solutions within this market, the reliability of the accelerometer avoids potential system bypass.


The most awarded access control reader around the world

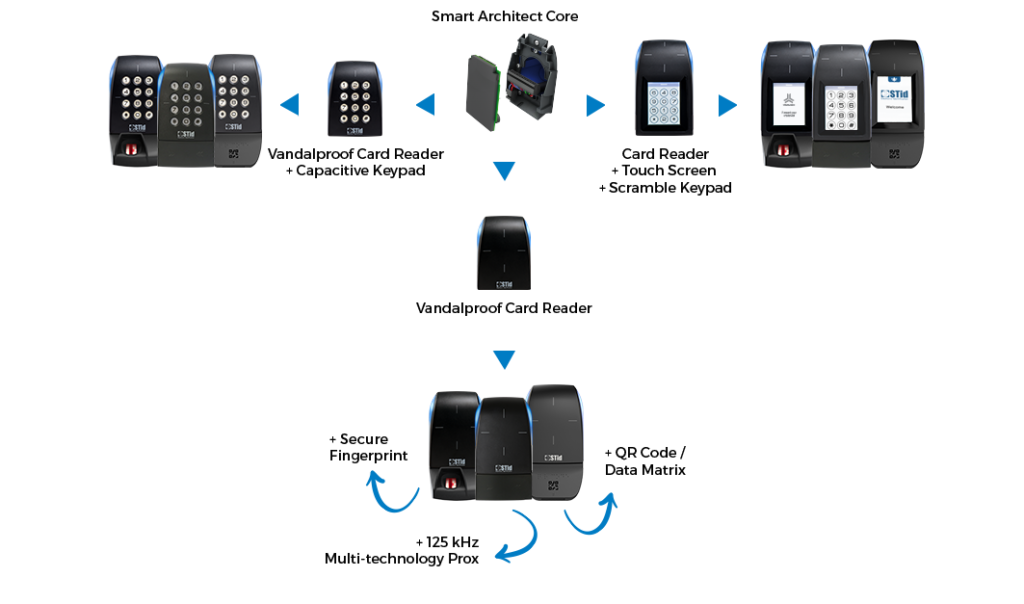
Create your own upgradable configuration
The Architect® Blue series is intuitive and dynamic, and consists of 6 interchangeable modules that can easily be connected to a common smart RFID core.
This easy and cost saving modular approach allows autonomy on the security access management.